Two-factor authentication provides a crucial layer of security, adding an extra shield against unauthorized access. It’s a powerful method for safeguarding accounts and sensitive data by requiring two forms of verification – something you know (like a password) and something you have (like a code from your phone). This approach dramatically reduces the risk of hacking, making it a fundamental practice for online security.
Understanding the intricacies of 2FA is key to effectively leveraging its benefits. This guide explores the diverse range of methods, implementation strategies, and security protocols associated with 2FA. We’ll delve into user experience considerations, common threats, and alternative approaches, ultimately equipping you with a comprehensive understanding of this essential security measure.
Introduction to Two-Factor Authentication
Two-factor authentication (2FA) is a security measure that adds an extra layer of protection to online accounts. It requires users to provide two different authentication factors, typically something they know (e.g., a password) and something they have (e.g., a security token). This significantly reduces the risk of unauthorized access compared to relying solely on passwords.The fundamental principle behind 2FA is to verify the user’s identity by requiring multiple forms of verification.
This approach makes it substantially more challenging for attackers to gain access, even if they successfully compromise one authentication factor. The key is the inherent difficulty of an attacker simultaneously obtaining both factors.
Types of Two-Factor Authentication Methods
Various methods are available for implementing 2FA, each with its own security characteristics. Some common methods include SMS-based codes, email-based codes, and hardware tokens. Each approach has unique strengths and weaknesses.
- SMS-based 2FA utilizes text messages to send one-time codes to a user’s registered phone number. This method is widely used due to its simplicity and widespread availability.
- Email-based 2FA relies on sending verification codes to the user’s registered email address. This approach, while simple, can be vulnerable to phishing attacks if the email account is compromised.
- Hardware tokens are physical devices that generate unique codes. These tokens offer high security as they are not reliant on network connections or email services. They can generate time-based one-time passwords (TOTP) or static codes.
Security Benefits of Using 2FA
Employing 2FA significantly strengthens the security posture of accounts and systems. This is achieved by creating a multi-layered defense mechanism that renders password breaches largely ineffective. Even if an attacker gains access to a user’s password, they still need to obtain the second factor to gain full access.
Authentication Factors Table
| Factor Type | Description | Security Considerations |
|---|---|---|
| Something you know | Passwords, PINs, security questions | Vulnerable to brute-force attacks, social engineering, and password reuse. |
| Something you have | Security tokens, mobile devices, authenticator apps | Vulnerability depends on the specific method; hardware tokens are generally more secure. |
| Something you are | Biometrics like fingerprint or facial recognition | Security depends on the implementation; potential for spoofing or data breaches. |
Implementation Strategies
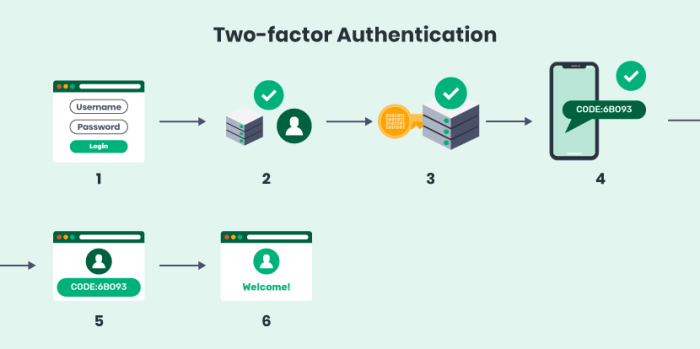
Implementing two-factor authentication (2FA) effectively across diverse platforms requires careful consideration of various factors. A well-designed 2FA system enhances security significantly, safeguarding user accounts and sensitive data from unauthorized access. Different methods cater to different needs and technical capabilities.Implementing 2FA involves a careful approach to user experience, system integration, and security considerations. The primary goal is to establish a robust and user-friendly system that minimizes friction while maximizing security.
Platform-Specific Implementation
Various platforms demand tailored 2FA implementations. Web applications, mobile apps, and desktop software each present unique challenges and opportunities. A crucial aspect is ensuring seamless user experience while maintaining security.
- Web Applications: 2FA integration into web applications typically involves using a dedicated authentication library or service. This library handles the secure exchange of authentication tokens and user verification. Often, a simple pop-up or redirection to a verification page is sufficient for user experience. An example includes a login page that prompts for a one-time code sent via SMS.
- Mobile Apps: Mobile applications leverage the unique capabilities of smartphones for enhanced security. Applications often use push notifications or authenticator apps for 2FA verification. These methods provide a more immediate and user-friendly experience compared to SMS-based codes. For example, an authenticator app generates a time-based one-time password (TOTP) that the user enters during login.
- Desktop Software: 2FA integration into desktop applications requires a different approach than web or mobile applications. The implementation needs to be integrated into the application’s core functionality. This could involve using dedicated libraries or SDKs to provide a secure 2FA mechanism. A typical example includes a desktop banking application that utilizes a hardware token for verification.
User Setup Procedure
A clear and concise setup process is crucial for user adoption. The process should be straightforward and intuitive, minimizing user frustration. The procedure should guide the user through the steps needed to set up and configure their 2FA method.
- Registration: The user initiates the setup process by selecting a preferred 2FA method (e.g., SMS, authenticator app). The system prompts the user to provide the necessary details, such as a phone number or email address.
- Verification: The system sends a verification code (e.g., via SMS or email) to the user’s registered device. The user enters the code into the system to confirm their identity.
- Confirmation: Upon successful verification, the system completes the setup process and prompts the user to confirm their 2FA setup. The system typically stores the user’s authentication method and details for future use.
Integration into Existing Systems
Integrating 2FA into existing systems can be achieved through various approaches. The chosen approach depends on the system’s architecture and the specific 2FA method being implemented.
- API Integration: For web applications and APIs, utilizing APIs to communicate with the 2FA provider is a common approach. This approach is adaptable and allows for flexibility in managing authentication details.
- Authentication Middleware: Employing a dedicated authentication middleware layer between the application and the authentication system streamlines the integration process and provides a centralized point for managing authentication protocols.
- Authentication Modules: Building or utilizing authentication modules specifically designed to support 2FA can simplify the integration process and ensure security standards are maintained.
Security Strengths and Weaknesses of Different Methods
Different 2FA methods offer varying levels of security and convenience. The selection of a specific method should be based on the system’s requirements and the user experience desired.
| Method | Security Strengths | Security Weaknesses |
|---|---|---|
| SMS-based | Widely accessible and readily available. | Vulnerable to SMS interception and SIM swapping. |
| Authenticator App | High security due to time-based one-time passwords (TOTP). | Reliance on a secure device and potential for device compromise. |
| Hardware Token | Extremely high security, difficult to compromise. | Requires physical possession and can be more expensive. |
Platform Integration Examples
This table illustrates different platform integrations with examples.
| Platform | 2FA Method | Example |
|---|---|---|
| Web Application (eCommerce) | SMS | User receives a 6-digit code via SMS after entering their login credentials. |
| Mobile Banking App | Authenticator App | User uses an authenticator app to generate a time-based one-time password (TOTP). |
| Desktop Email Client | Hardware Token | User inserts a hardware token to generate a verification code. |
User Experience and Design Considerations
Two-factor authentication (2FA) is a crucial security measure, but its effectiveness hinges significantly on the user experience. A poorly designed 2FA system can deter users from adopting it, leading to security vulnerabilities. A seamless and intuitive 2FA process fosters user trust and compliance.
User Frustrations and Pain Points
Common user frustrations stem from the additional steps required by 2FA. Delayed or interrupted login processes, unreliable authentication methods, and complex configuration steps are frequent sources of user dissatisfaction. Inconsistent or poorly worded error messages can further compound the problem, making it difficult for users to troubleshoot issues. Forgetting or losing backup codes, or issues with mobile device connectivity can also cause significant frustration.
Design Considerations for a User-Friendly 2FA Implementation
A user-friendly 2FA implementation prioritizes simplicity and reliability. Clear instructions and visual cues are essential to guide users through the process. Using familiar and intuitive interfaces minimizes user confusion and errors. Providing multiple authentication options offers flexibility and caters to diverse user preferences. The system should incorporate robust error handling with easily understandable messages, and include recovery options to address forgotten credentials.
Enhancing the User Experience with 2FA
Effective 2FA implementation requires a proactive approach to user experience. This involves careful consideration of the following factors:
- Intuitive Interface Design: A user-friendly interface is crucial for a smooth authentication process. Clear visual cues, concise instructions, and consistent design elements reduce user confusion and ensure ease of use.
- Multiple Authentication Methods: Offering diverse authentication methods, such as SMS, email, or authenticator apps, allows users to choose the method they find most convenient and secure. This caters to different user preferences and ensures continued accessibility.
- Robust Error Handling: Providing detailed and helpful error messages is critical. These messages should clearly identify the problem and guide users toward solutions, reducing frustration and improving user satisfaction.
- Backup Options and Recovery Procedures: Implementing backup options, such as recovery codes or email notifications, is essential for handling forgotten or lost credentials. Clear instructions and readily available recovery procedures mitigate security risks and user anxiety.
- Security Awareness Training: Educating users about 2FA best practices can improve their understanding and adoption of the system. This involves clear communication of the security benefits and how to avoid common security pitfalls.
UX Considerations and Solutions for 2FA Implementation
The table below Artikels key UX considerations and corresponding solutions for a successful 2FA implementation:
| UX Consideration | Solution |
|---|---|
| Simplicity and Clarity | Use clear, concise language and intuitive interface design. Provide visual cues and guidance at each step. |
| Accessibility and Flexibility | Offer multiple authentication methods (e.g., SMS, email, authenticator app). Ensure compatibility with various devices and operating systems. |
| Error Handling and Support | Implement robust error handling with easily understandable messages. Provide clear instructions for troubleshooting common issues. |
| Security and Recovery | Offer backup options (e.g., recovery codes, email notifications). Provide a secure and user-friendly recovery process. |
| Security Awareness | Offer educational materials and resources to promote security awareness. Communicate the security benefits of 2FA to users. |
Security Protocols and Best Practices
Robust security protocols are crucial for the effective implementation of two-factor authentication (2FA). A well-designed 2FA system not only enhances security but also safeguards user accounts from unauthorized access, mitigating the risk of account compromise. This section details the importance of these protocols, highlighting various attack vectors and best practices to secure 2FA implementations.
Importance of Security Protocols for 2FA
FA systems, by their very nature, rely on multiple layers of authentication. This multi-factor approach significantly increases the complexity for attackers, making unauthorized access substantially more difficult. A strong security protocol ensures that each authentication step is secure and resistant to common attacks. This prevents unauthorized access, protecting sensitive data and maintaining user trust.
Securing 2FA Implementation Against Attacks
Implementing robust security measures is paramount to thwarting potential attacks on 2FA systems. A comprehensive approach must consider various attack vectors, such as phishing attempts, man-in-the-middle (MITM) attacks, and brute-force attacks. These attacks exploit vulnerabilities in the authentication process, potentially bypassing the security measures and gaining unauthorized access.
- Phishing: Countermeasures against phishing attacks include educating users about suspicious emails and messages, implementing robust email filtering systems, and regularly monitoring for suspicious activity. This proactive approach can significantly reduce the risk of phishing attacks, which often aim to trick users into revealing their 2FA credentials.
- Man-in-the-Middle (MITM) Attacks: Secure communication channels, such as encrypted connections (HTTPS), are essential to protect against MITM attacks. Regularly updating software and employing strong encryption protocols helps mitigate the risk of intercepted authentication data.
- Brute-Force Attacks: Implementing rate limiting and account lockout policies can help mitigate brute-force attacks. These measures prevent automated attempts to guess user credentials, effectively deterring attackers who attempt to guess login details.
Secure Storage and Handling of 2FA Secrets
Safeguarding 2FA secrets is critical to maintain the integrity of the system. Secrets, such as recovery codes or backup phrases, must be stored securely and protected from unauthorized access. Compromised secrets can directly lead to account takeover.
- Storing Secrets: Secrets should be stored using strong encryption methods and access controls. Never store secrets in plain text, and consider using hardware security modules (HSMs) for enhanced protection.
- Handling Secrets: Establish clear protocols for accessing and handling 2FA secrets. Restrict access to authorized personnel and implement multi-factor authentication for sensitive operations involving these secrets.
Regular Security Audits for 2FA Systems
Regular security audits are essential for identifying vulnerabilities and ensuring the ongoing effectiveness of the 2FA system. Audits help identify potential weaknesses in the system’s design or implementation, which might be exploited by attackers.
- Frequency of Audits: Regular security audits, such as penetration testing and vulnerability assessments, should be conducted periodically to identify and address any vulnerabilities. The frequency of audits should align with the level of risk associated with the system.
- Types of Audits: Security audits can encompass various testing methodologies, including penetration testing to simulate real-world attacks and vulnerability scanning to identify potential weaknesses. These audits provide crucial insights into the system’s security posture.
Summary of Security Protocols, Threats, and Mitigation Strategies
| Security Protocol | Threat | Mitigation Strategy |
|---|---|---|
| Strong Encryption (HTTPS) | MITM Attacks | Implement HTTPS for all 2FA communication channels. |
| Rate Limiting | Brute-Force Attacks | Implement rate limiting to prevent automated attacks. |
| Multi-Factor Authentication (MFA) | Phishing, Password Guessing | Implement MFA for accessing 2FA secrets and sensitive operations. |
| Secure Storage | Unauthorized Access | Use strong encryption and access controls for secret storage. |
Common Security Threats and Vulnerabilities
Two-factor authentication (2FA) significantly enhances security, but it’s not impenetrable. Understanding the common threats and vulnerabilities associated with 2FA systems is crucial for robust implementation and effective mitigation strategies. This section details the potential pitfalls to consider when designing and deploying 2FA solutions.
Identifying Common Security Threats
FA systems are susceptible to a range of attacks, from sophisticated phishing schemes to simple vulnerabilities in the authentication methods themselves. Criminals exploit weaknesses in both the authentication process and the user’s interaction with it. This includes exploiting human psychology, social engineering, and exploiting vulnerabilities in the technical infrastructure.
Vulnerabilities in Different 2FA Methods
Different 2FA methods present unique vulnerabilities. SMS-based 2FA, for instance, relies on the user’s mobile phone’s network infrastructure, which can be compromised. Similarly, authenticator apps, while generally secure, are susceptible to malware infections or unauthorized access if the user’s device is compromised. Furthermore, vulnerabilities can lie within the underlying security protocols of the authenticator app or server itself.
Phishing Attacks and Their Relation to 2FA
Phishing attacks remain a significant threat to 2FA systems. Attackers often use social engineering tactics to trick users into revealing their 2FA codes or credentials. Phishing emails often mimic legitimate communication, exploiting trust and urgency. These attacks can be sophisticated and convincing, requiring users to exercise caution and critically evaluate any communication requesting personal information. Phishing attempts frequently target 2FA codes, either through compromised websites or malicious emails.
Two-factor authentication is a robust security measure, but advancements in computer vision technology are offering interesting new possibilities for enhancing it. For example, using facial recognition methods, similar to those found in Computer vision technology , could add a layer of security beyond just passwords and codes. This approach promises to make two-factor authentication even more secure and user-friendly.
Protecting Against Social Engineering Attacks
Robust security awareness training for users is essential in mitigating social engineering attacks. Training should emphasize the importance of verifying the legitimacy of communication requests and avoiding clicking suspicious links. Users should be educated about recognizing common phishing techniques and report any suspicious activity promptly. Multi-factor authentication (MFA) practices should be reinforced with rigorous training.
Table of Security Threats and Vulnerabilities
| Threat Category | Description | Example |
|---|---|---|
| Phishing | Deceptive communication to gain sensitive information. | A fake email claiming to be from a bank requesting login credentials and 2FA codes. |
| Man-in-the-Middle (MitM) Attacks | Interception of communication between the user and the authentication system. | An attacker intercepts SMS messages containing 2FA codes. |
| Malware Infections | Software designed to damage or gain unauthorized access to a system. | Malware installed on a user’s device that captures 2FA codes from authenticator apps. |
| SIM Swapping | Unauthorized access to a user’s mobile phone account. | An attacker gains access to a user’s phone number and uses it to receive 2FA codes. |
| Brute-Force Attacks | Repeated attempts to guess passwords or 2FA codes. | Automated tools used to try various combinations of 2FA codes. |
Security Auditing and Monitoring
Regular security audits and monitoring are crucial for maintaining the integrity and effectiveness of two-factor authentication (2FA) systems. These processes help identify vulnerabilities, assess risks, and ensure ongoing compliance with security best practices. Proactive monitoring allows for swift detection and remediation of potential threats, ultimately safeguarding user accounts and sensitive data.
Importance of Security Audits
Security audits provide a comprehensive evaluation of the 2FA system, examining its design, implementation, and operational procedures. This assessment helps identify weaknesses and gaps in security controls that might be exploited by malicious actors. Audits are vital for maintaining user trust and confidence in the system. They are essential for compliance with industry regulations and internal security policies.
Steps Involved in a 2FA Security Audit
A thorough 2FA security audit involves several key steps. These steps typically include:
- Reviewing the 2FA system’s design and architecture to identify potential vulnerabilities.
- Assessing the implementation of security controls, including authentication mechanisms and user access management.
- Testing the 2FA system’s resilience against various attack scenarios, such as phishing or brute-force attempts.
- Evaluating the system’s compliance with relevant security standards and regulations.
- Documenting all findings, including vulnerabilities, risks, and recommendations for improvement.
Importance of Log Analysis for 2FA Security
Log analysis plays a critical role in identifying and responding to security incidents related to 2FA. Detailed logs provide valuable insights into user activity, authentication attempts, and system behavior, allowing security teams to detect anomalies and potential threats. Analyzing these logs helps in understanding the patterns of attacks and vulnerabilities, enabling proactive measures to prevent future incidents.
Log Analysis Tools
The effectiveness of log analysis depends heavily on the tools used. Different tools cater to specific needs and data formats. A range of tools are available for analyzing logs related to 2FA.
| Tool | Use Cases |
|---|---|
| Splunk | Comprehensive log management and analysis, particularly useful for large volumes of data from diverse sources. |
| ELK Stack (Elasticsearch, Logstash, Kibana) | A popular open-source platform for log aggregation, searching, and visualization. |
| Graylog | A versatile open-source log management system suitable for analyzing logs from various applications and devices. |
| LogRhythm | A commercial security information and event management (SIEM) platform focused on threat detection and incident response. |
Monitoring 2FA System Performance
Monitoring 2FA system performance is vital for ensuring smooth operation and user experience. This includes tracking key metrics such as authentication success rates, authentication times, and error rates. Regular monitoring allows for timely identification of performance bottlenecks and system issues. It also helps in identifying and addressing issues related to user experience and satisfaction.
Alternative Authentication Methods
Beyond the familiar two-factor authentication (2FA) methods, a variety of alternative approaches are emerging. These methods aim to improve user experience, enhance security, and address specific limitations of traditional 2FA. Exploring these alternatives allows for a more comprehensive understanding of the authentication landscape and the potential for future advancements.Alternative authentication methods offer diverse approaches to verifying user identities.
They range from leveraging existing user data to employing cutting-edge technologies. Understanding their strengths and weaknesses is crucial in selecting the most appropriate method for a given application or system.
Biometric Authentication
Biometric authentication leverages unique physiological or behavioral characteristics to verify identity. This method often surpasses traditional password-based systems in terms of security, as it’s inherently difficult to replicate. However, it’s crucial to carefully consider the privacy implications and potential for misuse.
- Fingerprint Scanning: This widely adopted method uses the unique patterns of ridges and valleys on a fingertip. It offers high security and convenience, though concerns about spoofing attempts remain. Furthermore, environmental factors like moisture or cuts can affect the accuracy of scanning.
- Facial Recognition: Facial recognition technology analyzes facial features to verify identity. It’s increasingly prevalent in various applications, offering convenience and speed. However, the security of facial recognition systems is contingent on the sophistication of the algorithm and the robustness of the data collection and storage processes.
- Voice Recognition: This method utilizes voice patterns to authenticate users. It’s particularly useful in applications requiring hands-free authentication. However, environmental noise and variations in the user’s voice can impact accuracy. Careful consideration of the noise-canceling features of the technology is needed.
One-Time Passwords (OTPs) via Different Channels
One-Time Passwords (OTPs) provide a strong layer of security, especially when combined with other authentication methods. Instead of relying solely on a static password, OTPs generate unique codes for each login attempt. This adds an extra layer of security against unauthorized access.
- SMS-based OTPs: Widely used, these codes are delivered via SMS messages. While convenient, they are vulnerable to SIM swapping attacks and can be less secure than other methods. Security vulnerabilities need to be addressed through robust SIM card security measures.
- Email-based OTPs: Email-based OTPs are a viable alternative, but email accounts can be vulnerable to hacking. This means implementing security measures like strong email passwords and two-factor authentication for email accounts is critical.
- Hardware Tokens: These physical devices generate OTPs and enhance security significantly. They are generally more secure than SMS-based OTPs, as they are less susceptible to interception. However, they require a dedicated hardware device, which can increase costs.
Other Alternative Methods
Beyond biometric and OTP methods, other alternatives are emerging. These methods focus on reducing friction and enhancing user experience.
| Authentication Method | Description | Pros | Cons |
|---|---|---|---|
| Location-Based Authentication | Verifies the user’s physical location. | High security in restricted areas, reduces risks. | User privacy concerns, location tracking issues. |
| Behavioral Biometrics | Authenticates based on user’s typing patterns or mouse movements. | Unique behavioral patterns offer high security, user convenience. | Potential for spoofing or adaptation, requires extensive data collection. |
| Challenge-Response Systems | Verify user knowledge or actions. | Adaptable to different user profiles and situations, user familiarity. | Requires a secure mechanism for distributing challenges, security weaknesses possible. |
Mitigating Phishing Attacks
Phishing attacks targeting two-factor authentication (2FA) are a significant threat to online security. These attacks exploit user trust and often leverage social engineering tactics to trick users into divulging their sensitive authentication credentials. Effective mitigation strategies require a multi-faceted approach encompassing user education, robust security protocols, and proactive security monitoring.Implementing robust security measures, coupled with comprehensive user education, is crucial to thwarting phishing attempts.
This involves equipping users with the knowledge and skills to recognize fraudulent communications, thereby preventing unauthorized access to their accounts.
User Education for Phishing Awareness
User education plays a critical role in countering phishing attempts targeting 2FA. Users need to be educated about the characteristics of phishing emails, messages, or websites. This includes recognizing subtle variations in legitimate communication, understanding the methods employed by attackers, and comprehending the importance of verifying the authenticity of requests for personal information. This includes training on identifying suspicious email addresses, unusual formatting, and grammatical errors, which are often telltale signs of phishing attempts.
Security Awareness Training for 2FA Protection
Security awareness training is essential to equip users with the knowledge and skills to identify and avoid phishing attempts that target 2FA. Training programs should emphasize recognizing phishing tactics, including spoofed emails, fraudulent websites, and malicious links. These programs should also cover the importance of never sharing personal information, including 2FA codes, via unsolicited communications.
Anti-Phishing Techniques
Educating users is crucial, but implementing practical measures to mitigate phishing attacks is equally important.
| Technique | Description | Example |
|---|---|---|
| Email Filtering | Implementing filters to block emails containing suspicious s or links. | Blocking emails containing phrases like “verify your account” or “urgent security alert”. |
| Multi-Factor Authentication (MFA) | Requiring multiple authentication steps beyond a username and password, making it harder for attackers to gain access. | Using a code sent via SMS or a dedicated authentication app in addition to a password. |
| Domain Validation | Verifying the authenticity of a website’s domain through methods like Secure Sockets Layer (SSL) certificates. | Checking for the padlock icon in the browser’s address bar and verifying the domain name’s spelling. |
| Security Awareness Campaigns | Regularly informing users about the latest phishing techniques and best practices for recognizing and reporting suspicious communications. | Regular newsletters, in-house emails, and posters highlighting common phishing techniques. |
Multi-Layered Defense Mechanisms
Implementing multi-layered defense mechanisms is crucial for thwarting phishing attempts targeting 2FA. This involves a combination of technical safeguards and user training. A multi-layered approach is essential to protect against the various techniques used by attackers. These include proactive measures like regular security audits, automated email filtering, and user training to enhance user awareness.
“A layered security approach provides a more robust defense against phishing attacks targeting 2FA.”
Hardware Security Keys
Hardware security keys are physical devices that provide a strong second factor for authentication, enhancing the security of two-factor authentication (2FA) systems. They act as a physical barrier against phishing attacks and account takeovers, offering a significantly more secure authentication method compared to relying solely on software-based authentication methods.These keys offer a robust alternative to passwords, reducing the risk of credential compromise and associated security breaches.
They are particularly crucial for protecting sensitive accounts and systems, ensuring that only authorized individuals can access them.
Security Advantages of Hardware Security Keys
Hardware security keys offer numerous security advantages. They eliminate the reliance on easily compromised passwords, mitigating the risk of phishing and credential stuffing attacks. These devices, by their physical nature, are difficult to replicate or compromise, leading to a substantial improvement in overall security posture. Furthermore, they operate independently of the network and computer, increasing resistance to malware and other cyber threats.
Critically, they are less susceptible to social engineering tactics, as the physical device must be present for successful authentication.
Types of Hardware Security Keys
Various types of hardware security keys are available, each with specific functionalities and security features. Common types include USB-based keys, NFC-based keys, and Bluetooth-based keys. USB-based keys are the most prevalent, offering a tangible physical presence for authentication. NFC keys, utilizing near-field communication, enable contactless authentication. Bluetooth-based keys facilitate authentication through wireless connectivity.
Comparison of Hardware Security Keys
| Feature | USB-based | NFC-based | Bluetooth-based |
|---|---|---|---|
| Connectivity | USB connection | NFC proximity | Bluetooth wireless |
| Portability | Moderate | High | High |
| Ease of use | Generally easy | Very easy | Easy, potentially requiring pairing |
| Security | Strong, physical protection | Strong, physical protection | Strong, physical protection |
| Cost | Variable | Variable | Variable |
The table above provides a basic comparison of the different types. Each type has its own strengths and weaknesses, and the best choice depends on the specific use case and security requirements.
How Hardware Security Keys Enhance 2FA Security
Hardware security keys provide a significant boost to 2FA security by introducing a physical layer of authentication. This physical layer enhances security by making it harder for attackers to gain unauthorized access. This is because the attacker needs both the compromised credentials and the physical key, significantly increasing the difficulty of a successful attack. Critically, the physical presence of the key prevents credential stuffing attacks and other methods reliant on stolen credentials.
Integration with Existing Systems
Integrating two-factor authentication (2FA) into existing software systems requires careful planning and execution. A seamless integration ensures a smooth user experience and maintains the security posture of the application. This process must be approached methodically, considering potential disruptions and ensuring minimal impact on the user base.Integrating 2FA involves adapting existing authentication flows to include the second factor. This may necessitate changes to user interfaces, backend processes, and security protocols.
Careful consideration of the chosen 2FA method, such as SMS, email, or hardware tokens, is critical for optimal implementation.
Integration Process Overview
The successful integration of 2FA hinges on a well-defined process. This involves analyzing the existing system’s architecture, identifying points for 2FA insertion, and designing the appropriate user interface elements.
Integration Strategies for Different Systems
Different software systems have varying architectures and requirements. Adapting 2FA integration strategies to these systems is crucial for a smooth transition. For example, web applications typically involve modifying server-side code and potentially the front-end interface to handle the 2FA challenge. Mobile applications might require adjustments to the application’s architecture and potentially integration with platform-specific authentication APIs. Cloud-based systems may leverage existing cloud security features or require custom integrations with 2FA providers.
Step-by-Step Integration Procedure
A structured approach is vital for integrating 2FA into a system. The following table Artikels a general procedure:
| Step | Action | Description |
|---|---|---|
| 1 | Assessment | Analyze the existing system’s architecture, authentication flow, and user base. Identify potential integration points and dependencies. |
| 2 | Planning | Select the appropriate 2FA method (e.g., SMS, email, hardware token). Design the user interface for the 2FA process, ensuring usability and security. |
| 3 | Development | Modify the server-side code to handle the 2FA challenge. Implement the chosen 2FA method’s API calls or integrations. Test the integration thoroughly with various user scenarios. |
| 4 | Testing | Rigorous testing is essential. Conduct unit, integration, and user acceptance testing to identify and resolve potential issues. Test for security vulnerabilities. |
| 5 | Deployment | Roll out the 2FA implementation in stages to minimize disruptions. Monitor system performance and user feedback closely. |
| 6 | Monitoring | Continuously monitor system logs and user activity for any suspicious behavior. Review and update security protocols as needed. |
Examples of Integrating 2FA with Common Applications
Integrating 2FA with common applications like email clients, online banking platforms, and cloud storage services often involves modifications to existing authentication mechanisms. For example, an online banking application might require users to enter a one-time code sent via SMS or an authenticator app after entering their username and password. Cloud storage services often integrate 2FA through a dedicated authenticator app or hardware security key.
Two-factor authentication is a crucial step in bolstering security, especially when considering ransomware prevention. Implementing robust security measures, like those detailed in Ransomware prevention , can significantly reduce the risk of cyberattacks. Ultimately, two-factor authentication provides a critical layer of defense against such threats.
Future Trends in 2FA
Two-factor authentication (2FA) is constantly evolving to address emerging threats and user expectations. This evolution is driven by advancements in technology, user behavior, and the increasing sophistication of cyberattacks. Understanding these trends is crucial for maintaining strong security postures and anticipating future design requirements.
Emerging Technologies and Enhanced 2FA
Emerging technologies offer promising avenues for enhancing 2FA security and user experience. These include biometric authentication methods, such as fingerprint scanning and facial recognition, alongside advancements in hardware security keys. Leveraging these technologies can strengthen the security posture of 2FA implementations.
Biometric Authentication Methods
Biometric authentication methods, utilizing unique physical characteristics, are increasingly being integrated into 2FA systems. Fingerprint scanning, facial recognition, and iris scanning offer high levels of security due to the unique and difficult-to-replicate nature of these characteristics. However, concerns about privacy and potential security vulnerabilities associated with biometric data collection need careful consideration and mitigation strategies.
Hardware Security Keys
Hardware security keys, small physical devices, are becoming more prevalent as a robust second factor in 2FA. These keys offer a high level of security, as they are tamper-resistant and eliminate reliance on potentially vulnerable software-based solutions. The growing adoption of hardware security keys reflects a trend toward stronger security measures.
Integration with Existing Systems
The seamless integration of new 2FA methods into existing systems is crucial. This ensures a smooth transition for users without disrupting existing workflows. Efficient integration strategies are necessary for widespread adoption and the successful implementation of future 2FA designs.
Potential Future Trends in 2FA, Two-factor authentication
| Trend | Potential Impact on Security | Influence on Future 2FA Design |
|---|---|---|
| Increased use of biometrics | Enhanced security, but potential privacy concerns. | Design incorporating biometric security measures with robust privacy protocols. |
| Focus on user experience | Improved user adoption, reduced friction. | Design emphasizing simplicity, convenience, and ease of use for all users. |
| Integration with emerging technologies (e.g., blockchain) | Increased security, enhanced trust, and transparency. | Design integrating blockchain technology for enhanced security, transparency, and trust. |
| Emphasis on multi-factor authentication (MFA) | Significantly stronger security posture. | Design incorporating MFA as a standard approach to authentication. |
Elaboration on Emerging Technologies
Advancements in hardware security keys are a notable trend. These keys, acting as physical tokens, provide a strong barrier against phishing attacks and other malicious activities. The integration of these keys into 2FA systems is a significant step towards robust security. Further, leveraging emerging technologies like blockchain in 2FA systems could provide enhanced transparency and security, by recording authentication events on a secure and immutable ledger.
Examples of companies incorporating these approaches already exist. Furthermore, the potential for incorporating these technologies into existing systems will be a major driver for future 2FA designs.
Wrap-Up

In conclusion, two-factor authentication is a critical component of modern security. By combining knowledge and possession factors, it significantly strengthens the defenses against unauthorized access. The detailed exploration of implementation strategies, security considerations, and alternative methods provides a comprehensive understanding of this essential security tool. Implementing robust 2FA practices is paramount for safeguarding sensitive information and accounts in today’s digital landscape.
Popular Questions
What are the common security threats targeting 2FA systems?
Phishing attacks, social engineering, and brute-force attempts are common threats. Compromised devices or weak security protocols can also be vulnerabilities.
What are some alternative authentication methods besides traditional 2FA?
Biometric authentication, such as fingerprint or facial recognition, and one-time passwords (OTPs) generated via different methods are alternatives. Hardware security keys offer a very strong level of security.
How can I educate users about recognizing phishing attempts related to 2FA?
Security awareness training is crucial. Educate users on spotting suspicious links, emails, and requests. Highlight the importance of verifying requests from official sources.
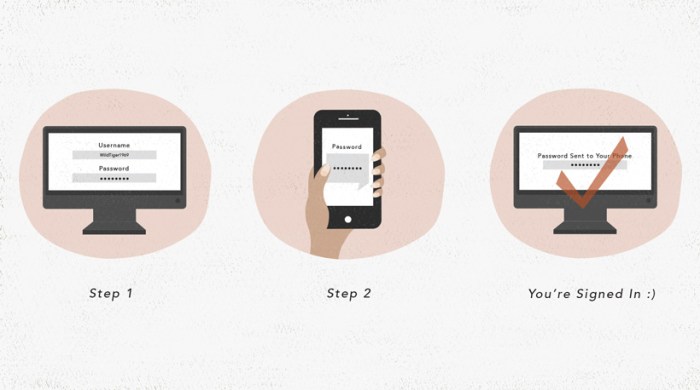
What are the steps involved in setting up 2FA for a typical user?
The setup process typically involves linking a secondary device (phone, hardware token) to your account. You’ll usually receive a verification code, which you’ll then enter to complete the setup.






